Name: Stella Gift ORIJI
Profile: Cybersecurity Professional and a Software Engineer
Email: stellagiftoriji@gmail.com
Phone: +234 (703)8395145
Some of my Skills
Next.JS 82%About me
I'm a certified cybersecurity analyst and a software engineer. My specializations are in Vulnerability Assessment and Penetration Testing, software development and security, smart contract development and deployment. I bring expertise in data driven analysis, backend development, and Security engineering. Certified by the International Information Systems Security Certification Consortium (ISC)², I excel in implementing the Confidentiality, Integrity, and Availability (CIA) Triad, along with SIEM, NAC, IAM, and the OWASP Framework. I am proficient in Python, SQL, Next.JS, Node.JS, React, Typescript, splunk and modern development and security technologies. I build secure, efficient software systems that integrate both analytical precision and cybersecurity resilience. I am available to hear your ideas and how I can help bring those to life. Helping your products stay secure from cyber adversaries through preemptive security and innovative solutions is the guiding light of my career journey.
Services
These are some of the services I offer.
Cybersecurity
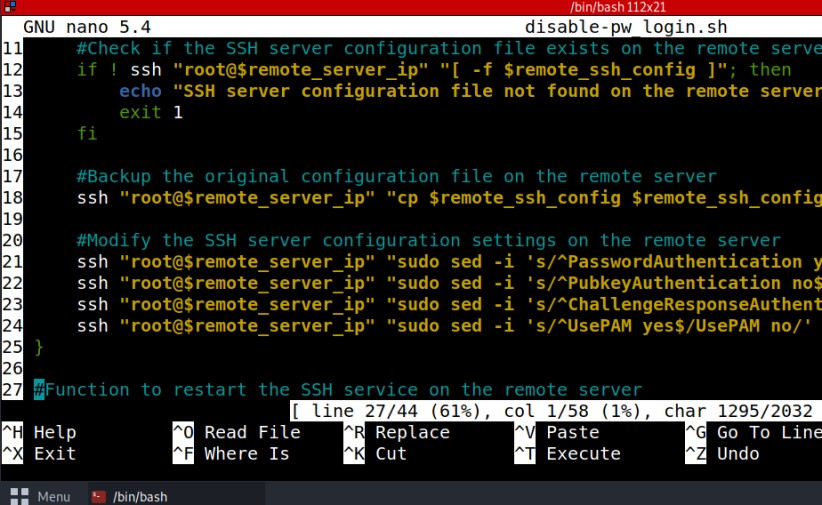
I utilize my expertise to safeguard computer systems and networks. I analyze vulnerabilities, implement security measures, and continuously monitor for threats. I respond to incidents, ensuring the protection of sensitive data and maintaining the Confidentiality, Integrity and Availability of information systems.
Vulnerability Assessment and Penetration Testing
I proactively identify and assess security vulnerabilities in computer systems, networks, or applications through systematic scans and ethical cyberattack simulations within permitted scopes. Using robust tools, I analyze results, providing insights and recommendations to enhance cybersecurity resilience by preemptively addressing potential weaknesses and strengthening overall security defenses.
Cybersecurity/IT Consultation and Education
I provide expert advice on IT matters and conduct educational activities such as training sessions or workshops for schools, individuals and organizations. I assist businesses in optimizing IT infrastructure and enhance individuals' or organizations' knowledge and skills in information technology.
Software Development
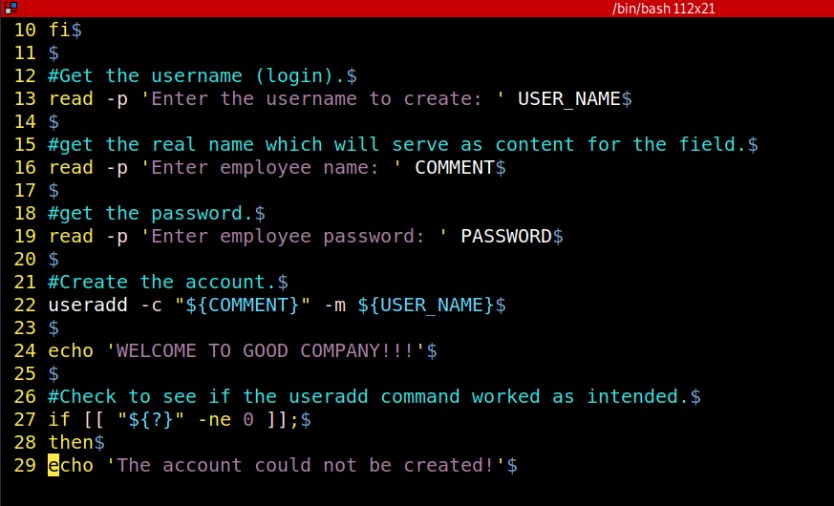
I develop efficient, user-focused and user-friendly software solutions tailored to deliver actual results and solve real world problems. From sleek web/mobile applications to secure backend systems. My work combines clean code, modern technologies, security solutions and intuitive design to deliver reliable, scalable, and high performing digital products. .
Smart Contract development/Deployment
I design, develop, and deploy secure and optimized smart contracts that power decentralized applications. I focus on creating transparent, efficient, and tamper-proof blockchain solutions that ensure trust, automation, and seamless interaction across Web3 ecosystems. .
DevOps
I streamline collaboration between development and operations teams. I automate processes, implement continuous integration/delivery, and enhance overall software delivery efficiency. By integrating tools and fostering collaboration, I aim to achieve faster, reliable, and more efficient software releases.
Projects
THESE ARE SOME OF THE PROJECTS I HAVE COMPLETED.
Blog
My thoughts articulated
Technology
Identity and Access: Unveiling Lapses in Nigeria’s Fintech IAM Practice
Implementing proper Access Control mechanism that aligns with user experience in Digital Products Architecture.
INTERNET
How your interaction with the internet works
What Happens When You Type https://www.google.com in Your Browser and Press Enter?
Cybersecurity
ProxyChains: Enhancing Anonymity and Security in Network Communications
Staying Anonymous While Using the Internet With Proxychain.